Google Cloud Fundamentals: Core Infraestructure - Resource and access in the cloud -> Services accounts

If you want to give permissions to a Compute Engine virtual machine, rather than to a person, that's what service accounts are for. Let’s say you have an application running in a virtual machine that needs to store data in Cloud Storage, but you don’t want anyone on the internet to have access to that data – just that particular virtual machine. You can create a service account to authenticate that VM to Cloud Storage.
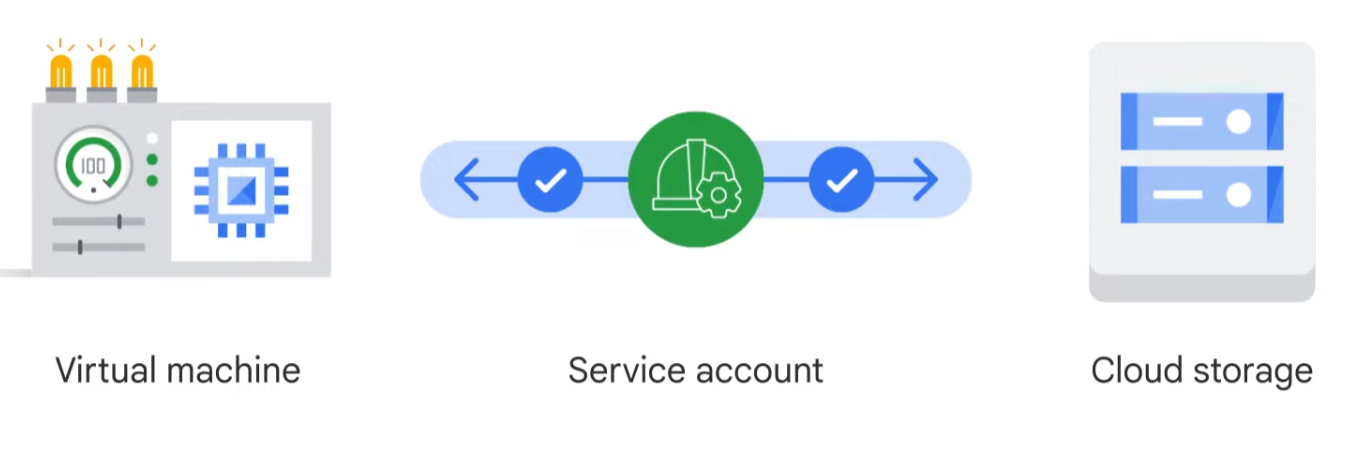
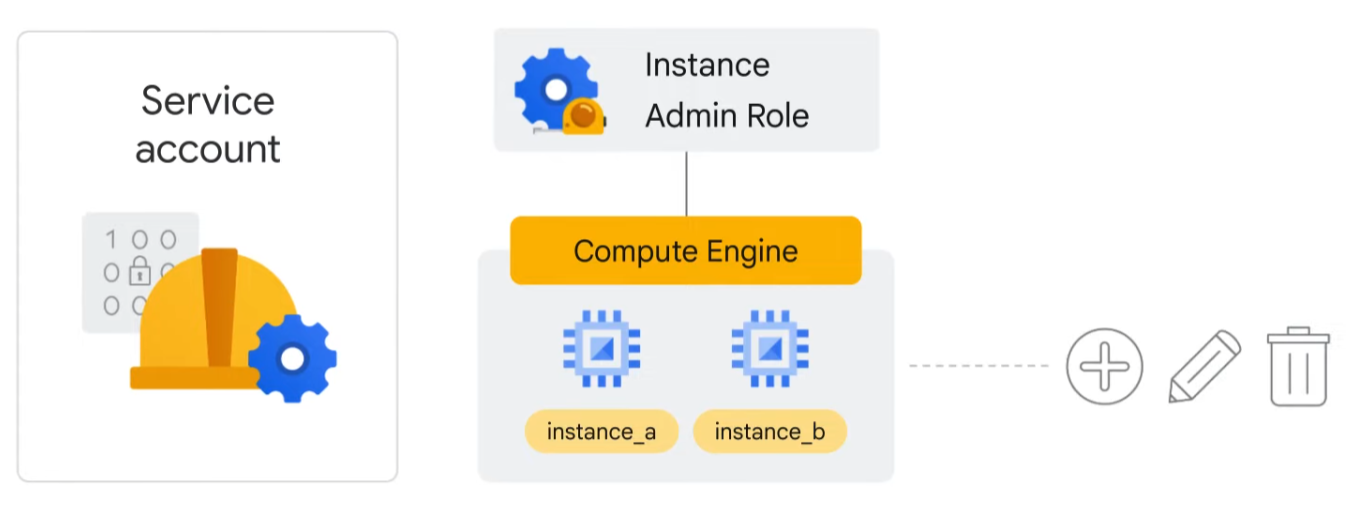
Service accounts are named with an email address, but instead of passwords, they use cryptographic keys to access resources. So, if a service account has been granted Compute Engine’s Instance Admin role, this would allow an application running in a VM with that service account to create, modify, and delete other VMs.
Service accounts do need to be managed. For example, maybe Alice needs to manage which Google accounts can act as service accounts, while Bob just needs to be able to view a list of service accounts. Fortunately, in addition to being an identity, a service account is also a resource, so it can have IAM policies of its own attached to it. This means that Alice can have the editor role on a service account, and Bob can have the viewer role. This is just like granting roles for any other Google Cloud resource.